Requested Item
XML error in File: http://topgfx.com/forum/subscribe-5.xml
XML error: Opening and ending ...
NDonate And Become A VIP
Contact Us
Administrators:
admin - Site/Tech Issues/ Member Issues/ VIP Issues
Mac - Site/Tech Issues
WuTeVa - Member Issues
Moderators:
BigBrother - Forum, Posting or Comment Problem
vrxitachi - Forum, Posting or Comment Problem
Don_k - Forum, Posting or Comment Problem
DropsOfJupiter - Forum, Posting or Comment Problem
Share Your Render
Chat Box
Send Me PM for any Kind Of Help
¹ New Categories
¹ Old Categories
O Top Rated Articles
Post Calendar
Partner Site
Top News
 TX Lujan Premium Pack for G9 G8 G8.1
TX Lujan Premium Pack for G9 G8 G8.1
 Lisa A extra H+B+T for Genesis 8 f
Lisa A extra H+B+T for Genesis 8 f
 Moreegan extra H+B+T package for Genesis 8 f
Moreegan extra H+B+T package for Genesis 8 f
 Leia 9 for Genesis 9
Leia 9 for Genesis 9
 Mideva for Genesis 8 Female (Update Ver)
Mideva for Genesis 8 Female (Update Ver)
 dForce Satin Pyjamas Set for Genesis 9
dForce Satin Pyjamas Set for Genesis 9
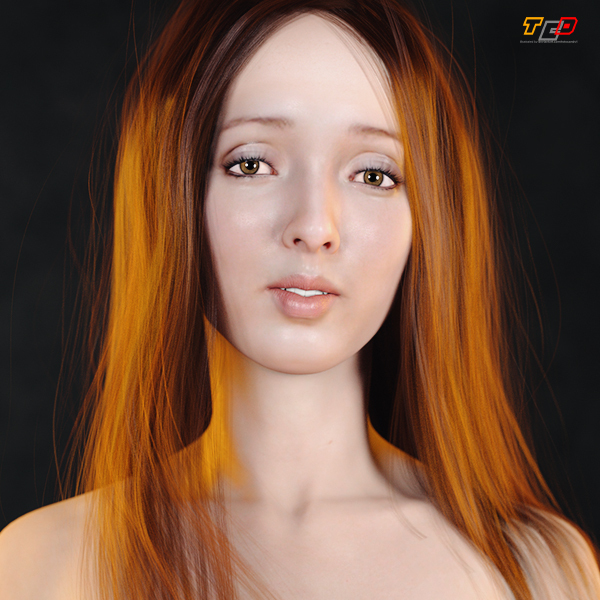 Lucie W extra H+B+T for Genesis 8 f
Lucie W extra H+B+T for Genesis 8 f
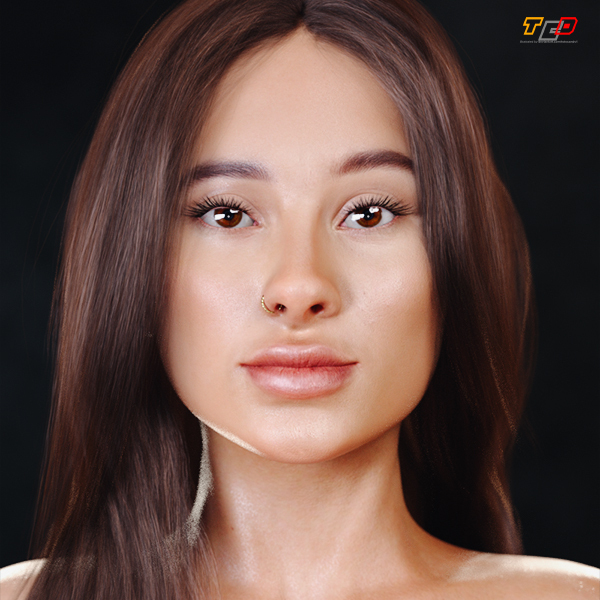 Sliva Bundle Package For Genesis 8 F
Sliva Bundle Package For Genesis 8 F
 RHK extra H+B+T package for Genesis 8 female
RHK extra H+B+T package for Genesis 8 female
 Bosah extra H+B+T package for Genesis 8 f
Bosah extra H+B+T package for Genesis 8 f
Latest Feed
XML error in File: https://news.google.com/news?q=3d%20modeling&output=rss
XML error: at line 0
Recent Searches
Server Time
Friday 3rd of May 2024 01:39:55 AM
Home
Contact Us
Basic Search on xtragfx.com
Edit Images Online
Advertise on Topgfx
Topgfx Sitemap
RSS Feed
Topgfx Free 3D Models » Others » Sam Bowne CNIT-123: Ethical Hacking And Network Defense
Sam Bowne CNIT-123: Ethical Hacking And Network Defense

Sam Bowne CNIT-123: Ethical Hacking And Network Defense | 1.4GB
Genre: VideoTraining
Lecture Notes and Projects (Spring 2008 Revision) by Sam Bowne
Catalog Description:
Students learn how hackers attack computers and networks, and how to protect systems from such attacks, using both Windows and Linux systems. Students will learn legal restrictions and ethical guidelines, and will be required to obey them. Students will perform many hands-on labs, both attacking and defending, using port scans, footprinting, exploiting Windows and Linux vulnerabilities, buffer overflow exploits, SQL injection, privilege escalation, Trojans, and backdoors.
Prerequisites:
CNIT 106 and 120 or equivalent familiarity with the fundamentals of networking and security.
Upon successful completion of this course, the student will be able to:
Explain what an ethical hacker can and can not do legally, and explain the credentials and roles of penetration testers.
Define the types of malicious software found in modern networks.
Explain the threats and countermeasures for physical security and social engineering.
Perform footprinting to learn about a company and its network.
Perform port scans to locate potential entry points to servers and networks.
Perform enumeration (finding resources, accounts, and passwords) on Microsoft, Netware, and Unix/Linux targets.
Perform very simple programming in C, HTML, and Perl, specifically oriented towards the needs of network security professionals.
Learn how to identify Microsoft Windows vulnerabilities and to harden systems.
Learn how to identify Linux vulnerabilities and to protect servers.
Describe how to take control of Web Servers, and how to protect them.
Locate and hack into wireless networks, and protect them.
Explain how cryptography and hashing work, and perform attacks against them such as password cracking and man-in-the-middle attacks.
Describe and deploy security devices, including routers, firewalls, Intrusion Detection Systems, and honeypots.
Download from Hotfile
http://hotfile.com/list/472475/3bf6ed2
Download from Shareflare
http://shareflare.net/download/7586.736805547b6da7a54396f7c300c4bec5/S.Bowne.CNIT.part13.rar.html
http://shareflare.net/download/2660.24613c19fae83388d0eebce367541e71/S.Bowne.CNIT.part14.rar.html
http://shareflare.net/download/1245.19b7b44cb5aaac1e36261061bddfc4a1/S.Bowne.CNIT.part09.rar.html
http://shareflare.net/download/2528.2dbd15a1b49eb2c44a3b4c0e2041f525/S.Bowne.CNIT.part11.rar.html
http://shareflare.net/download/8246.8fd125967b6101f085daf9fa0660f601/S.Bowne.CNIT.part12.rar.html
http://shareflare.net/download/8779.8c73b60971c8116c55bbbff0191e0218/S.Bowne.CNIT.part10.rar.html
http://shareflare.net/download/1724.1cc145229d787380de8c61d12a16ab4e/S.Bowne.CNIT.part08.rar.html
http://shareflare.net/download/1929.180e2601b61757ebbcc59b3b39a6438d/S.Bowne.CNIT.part05.rar.html
http://shareflare.net/download/6772.6aa6e106e548f072c4d1e9ec4bca9706/S.Bowne.CNIT.part07.rar.html
http://shareflare.net/download/8661.8c84fc17e5af1a01fb50f0b27b620ffc/S.Bowne.CNIT.part06.rar.html
http://shareflare.net/download/5940.55918d7baf799cd247a6efc1461b75b7/S.Bowne.CNIT.part03.rar.html
http://shareflare.net/download/6415.6af9b2456fb1547e8923d03138b885ee/S.Bowne.CNIT.part01.rar.html
http://shareflare.net/download/7446.7004ca9a53f35b80d05ec14457fbd982/S.Bowne.CNIT.part04.rar.html
http://shareflare.net/download/8164.8275a076823ff53f1d412400bcd4bd8b/S.Bowne.CNIT.part02.rar.html
10X Speed Direct Download Sam Bowne CNIT-123: Ethical Hacking And Network Defense
Related News

|
Career Academy Hacking Penetration Testing And Countermeasures Training Career Academy Hacking Penetration Testing And Countermeasures Training | 3.18 GB These training videos will show you how to scan, test, hack and |

|
Certified Ethical Hacker (CEH) V6 Video Tutorial (Vol 4) Certified Ethical Hacker (CEH) V6 Video Tutorial (Vol 4) | 1.15 GB This class will immerse the student into an interactive environment where they |

|
Certified Ethical Hacker (CEH) V6 Video Tutorial (Vol 3) Certified Ethical Hacker (CEH) V6 Video Tutorial (Vol 3) | 596.03 MB This class will immerse the student into an interactive environment where they |

|
Certified Ethical Hacker (CEH) V6 Video Tutorial (Vol 2) | 2.16 GB Certified Ethical Hacker (CEH) V6 Video Tutorial (Vol 2) | 2.16 GB |

|
Certified Ethical Hacker (CEH) V6 Video Tutorial (Vol 1) | 1.85 GB Certified Ethical Hacker (CEH) V6 Video Tutorial (Vol 1) | 1.85 GB |
Information
Would you like to leave your comment? Please Login to your account to leave comments. Don't have an account? You can create a free account now.
Would you like to leave your comment? Please Login to your account to leave comments. Don't have an account? You can create a free account now.







